Fixing Tailscale routes on OpnSense
Overview
This project addresses a known issue where Tailscale static routes are lost on OPNsense following configuration changes to your tailnet. To ensure continuous network connectivity within your tailnet, I’ve developed a workaround that monitors the accessibility of a specified IP address within the tailnet. If the ping to this IP fails, indicating a potential loss of Tailscale static routes, the Tailscale service is automatically restarted to restore connectivity.
Security Disclaimer
Security is paramount, especially when modifications involve your firewall. I strongly advise against blindly trusting external sources, including this repository. Before implementing any changes, thoroughly review and understand the code. Your network’s security and integrity depend on due diligence.
Implementation Guide
- Clone the repo
1
git clone https://github.com/ChrisTracy/tailscaleTools /var/tailscaleTools
- Make the script executable
1
chmod +x /var/tailscaleTools/scripts/tailCheck.sh - Copy the configd action file (this is what calls the script and makes it show up in the GUI)
1
cp /var/tailscaleTools/config/actions_tailcheck.conf /usr/local/opnsense/service/conf/actions.d - Restart the configd service
1
service configd restart
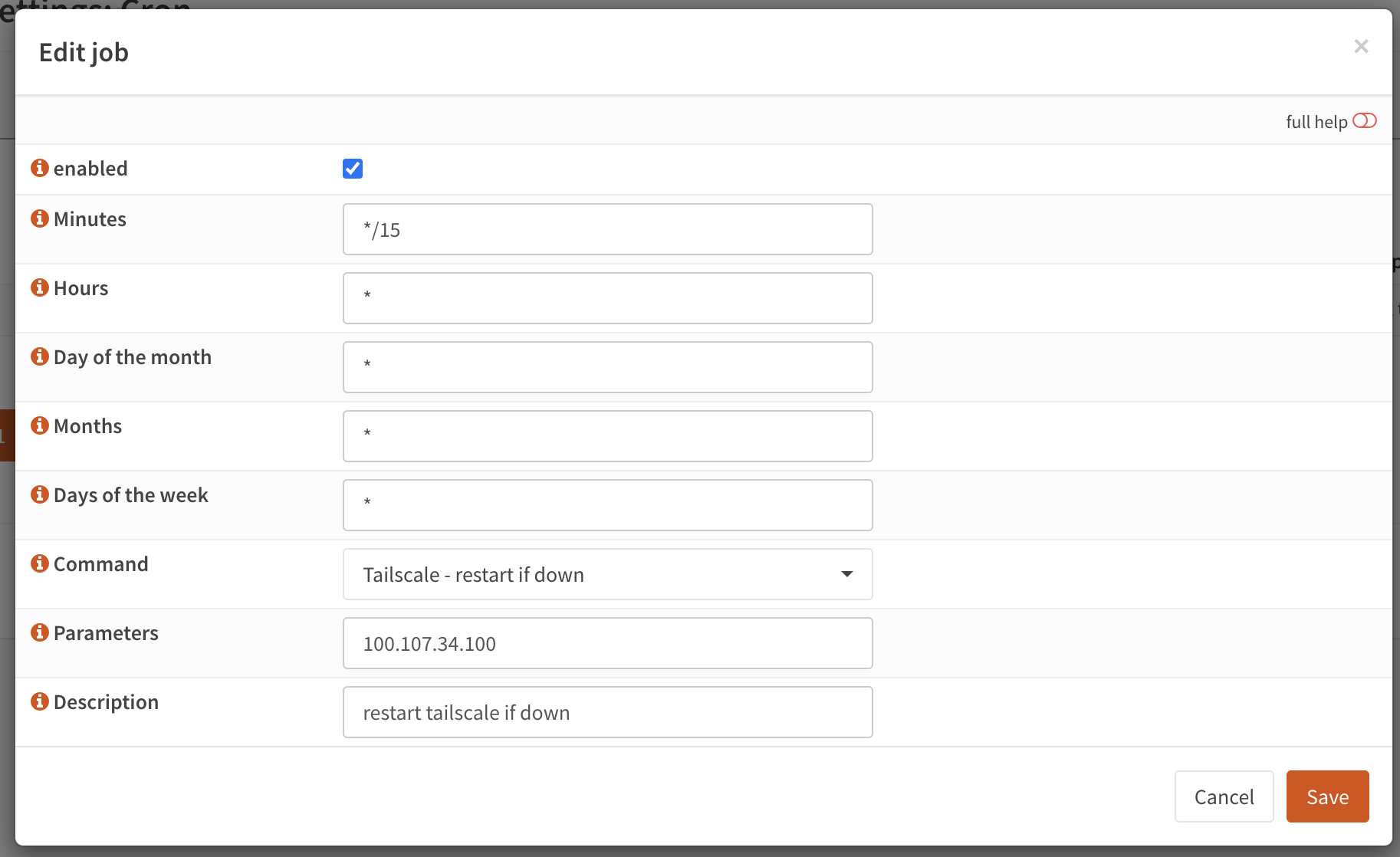
- Open the OPNsense GUI and navigate to System>Settings>Cron.
- Create a new cron job like the one below (mine is set to run every 15 minutes, adjust as needed).
- CHANGE THE PARAMETER FIELD TO A TAILNET IP THAT IS ALWAYS ONLINE IN YOUR TAILNET.
- Click Save
- Click Apply
- Wait until the next 15 minute mark on the hour (00,15,30,45) and check the log. You should see a “ping successful” or “Ping failed, restarting Tailscale service…” message.
1
cat /var/log/tailscaleTools/tailCheck.log